Cyber criminals have been emboldened by lax security barriers. This has resulted in a sharp increase in ransomware attacks which threaten businesses into parting ways with their money. In fact, governments worldwide saw an astronomical 1885% growth in ransomware attacks in 2021.
Because ransomware attacks are a combination of a digital robbery and blackmail wrapped into one, there is a heightened need for enterprise security to combat this issue. The legacy model of perimeter-based security was great for a pre-cloud era when data was localized to corporate data centers, but with the explosion of cloud service providers (CSPs), perimeter security is no longer feasible. Solution? Zero trust security.
What is the zero trust security model?
Coined by Forrester in 2010, the zero trust architecture model addresses the need for an enterprise security solution by emphasizing transaction-based security rather than blanket, implicit security. The model emphasizes transaction-based trust, i.e. “trust nothing and verify everything”.
Consider this example: An airport vendor whose kiosk is in the terminal crosses security gates multiple times each day. Given the frequency of back and forth movement, the vendor may even know the agents at the security checkpoint. Despite the vendor’s familiarity, they are still subject to the same rigorous security check every time they pass through the security gate as if they were entering for the first time.
In the same vein, any organization that implements zero trust security should be built to validate all client interactions and create micro-segments for their APIs and applications to minimize the blast surface.
Although zero trust architecture has been in use in the commercial sector for more than a decade, the model has since gained prominence within the public sector following the National Institute of Standards and Technology (NIST) release of a special publication discussing zero trust architecture in 2020. The publication highlights the importance of adopting zero trust architecture as a security posture to minimize the impact of ransomware attacks in the government sector and implementing zero trust architecture to secure agency data and applications.
Why do we need zero trust security?
Before the advent of the cloud (circa 2000), companies held their data and applications in private data centers, this was truly the only option. As long as the data center was protected, the company’s data and applications were safe. The relatively small perimeter of the data center made it easy to apply perimeter security both physically and digitally.
One side effect of perimeter-based security was implicit trust, a situation in which someone has a false sense of security that everything inside their corporate boundary is trustworthy.
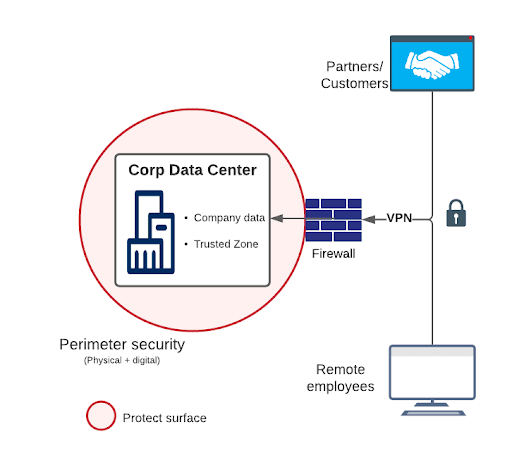
Modern businesses today are feverishly adopting cloud and SaaS applications, leading to a hybrid landscape where companies’ data are being distributed between corporate data centers and CSPs. This shared infrastructure is outside the absolute control of corporations. As corporations onboard new CSPs, the corporate perimeter continues to grow.
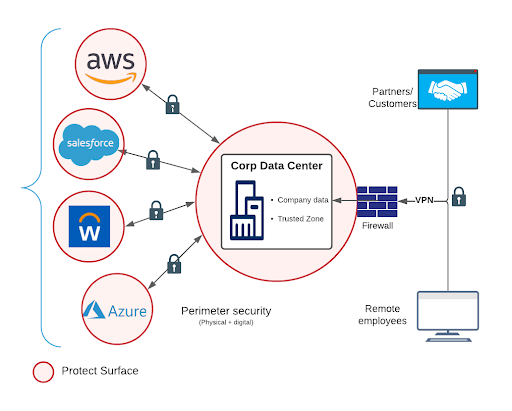
Limited control of CSPs’ infrastructure coupled with scattered data and ever-changing corporate boundaries means that the old way of perimeter-based security is no longer viable. Regardless of origin, transactions can no longer be implicitly trusted.
Tenets of zero trust security architecture
The implementation of zero trust architecture in Mule is predicated on the following principles:
- Use transaction-level security in addition to perimeter-based security. The perimeter security provides the first level of defense but is not sufficient enough in the changing landscape from on-premises to hybrid and cloud. It’s imperative that all transactions are vetted independently.
- Use zero trust policy and avoid implicit trust. Many organizations have been wrongly using implicit trust between applications from their pre-cloud days. As companies adopt cloud, it’s imperative that they eliminate implicit trust completely between the applications and enforce zero trust.
- Use layered security with micro-perimeters. Just like layered clothing provides better protection against extreme cold, a layered security provides better defense against security threats. Create micro-perimeters by careful segmentation of systems and applications thus reducing the exposed surface area.
- Dynamic security with continuous diagnostics and mitigation. Security is a cat and mouse game. As enterprises strengthen their security posture by using the latest and most advanced security products and architectures, so do the cyber criminals using increasingly sophisticated hacking techniques. So it’s necessary for organizations to continuously diagnose and mitigate threats.
Dangers of implicit trust
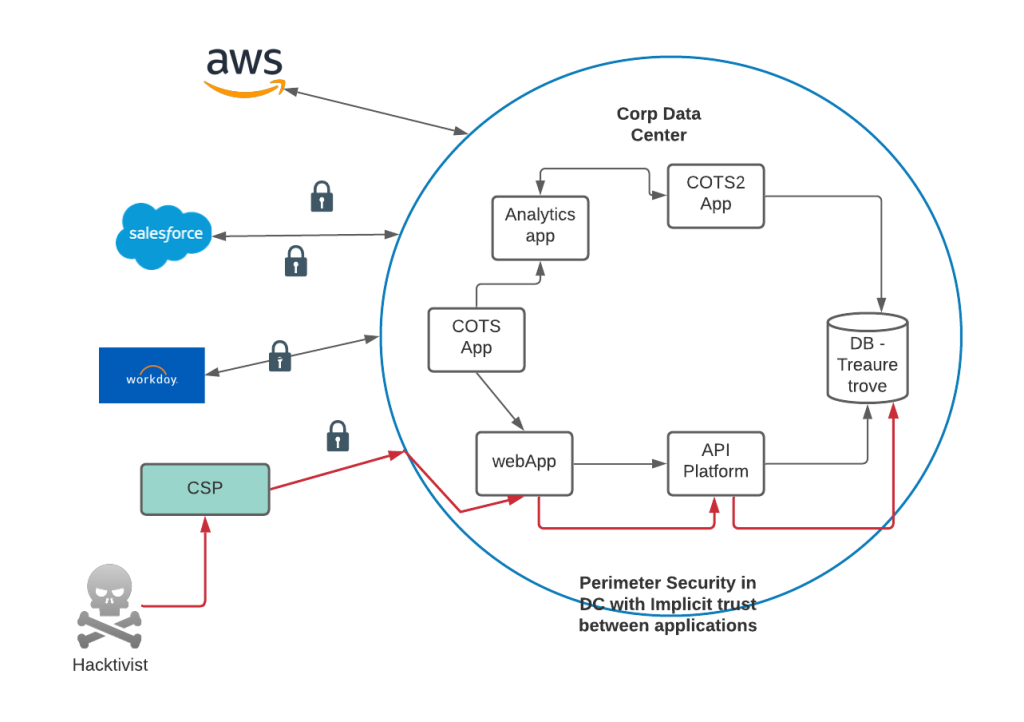
In a perimeter-based security trust model, applications automatically trust other applications inside a corporate network. Today, with the adoption of CSPs, the corporate network comprises corporate data centers and CSPs’ infrastructure as well.
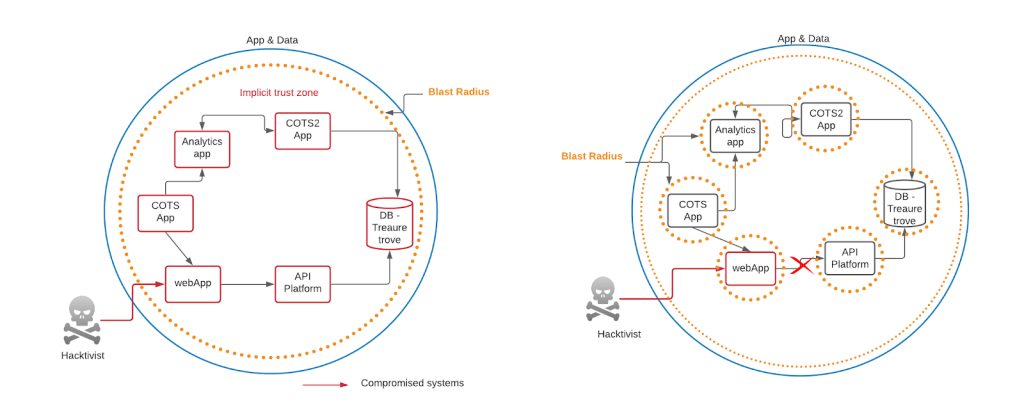
The ever-growing and vast corporate network opens up many avenues for hackers; potential weak links could be in the corporate data center or even a CSP, but their eventual target would be high value data. Implicit trust creates a domino effect as shown in diagram below, where one compromised application exposes multiple other critical applications, placing the entire corporation at risk.
Where does MuleSoft fit in the bigger picture?
In most digital-first companies, Mule is the backbone of the enterprise acting as a fabric connecting data and applications. Zero trust security requires a holistic approach covering the entire application stack of an enterprise – including Mule. So although zero trust architecture can’t be achieved by Mule alone, it plays a critical role by augmenting an organization’s zero trust security posture.
Think of it this way: the most important thing to remember when planning the defenses of a fort is to understand the fort. The doors, tunnels, height and thickness of the walls, and terrain all come into play in determining the defenses of the fort. In essence, understanding your application stack is critical in guaranteeing its security. API security is not just about endpoint protection it goes well beyond that.
Implementing zero trust architecture in Mule
Zero trust security architecture implementation in Mule is comprised of the following:
- Identifying the protect surface
- Implementing transaction-based trust
- Creating micro-perimeters
- Using granular permissions
- Initiating continuous diagnostics and mitigation
Let’s discuss each in more detail below.
Identifying the protect surface
Just like a Trojan horse, a security threat can creep in from anywhere, so identifying the protected surface is the most important aspect of zero trust security. In Mule, this means identifying the components of the Mule ecosystem which depends on Mule deployment options. The ownership of actual protection will depend on different teams from development, infrastructure, and network within an organization.
Implementing transaction-based trust
The initial airport example is a classic instance of transaction-based trust where there is no preordained implicit trust. This principle is one of the core tenets of zero trust security. Mule solutions typically involve following three interaction modes where transaction-based trust needs to be enforced:
| API to API | 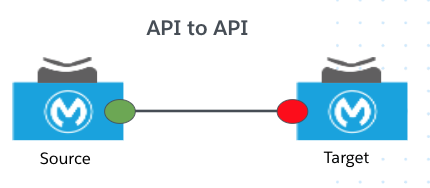 |
| API to target system |  |
| External system to API |  |
Mule provides outside-of-the-box policies like oAuth, Basic, and LDAP to implement transaction-based security. You can also use IP whitelisting/allowances and Mutual TLS (MTLS) to achieve security where suited.
Creating micro-perimeters
The diagram on the left shows a traditional perimeter-based security where there is implicit trust between applications in a data center. Here, a security compromise in any one application leads to a cascading effect, potentially compromising an entire organization.
The diagram on the right indicates a setup where a micro-segmentation is in effect and where a security compromise affects just one application thus containing the damage. Micro-perimeters reduce the blast radius, minimizing the impact of a security compromise.
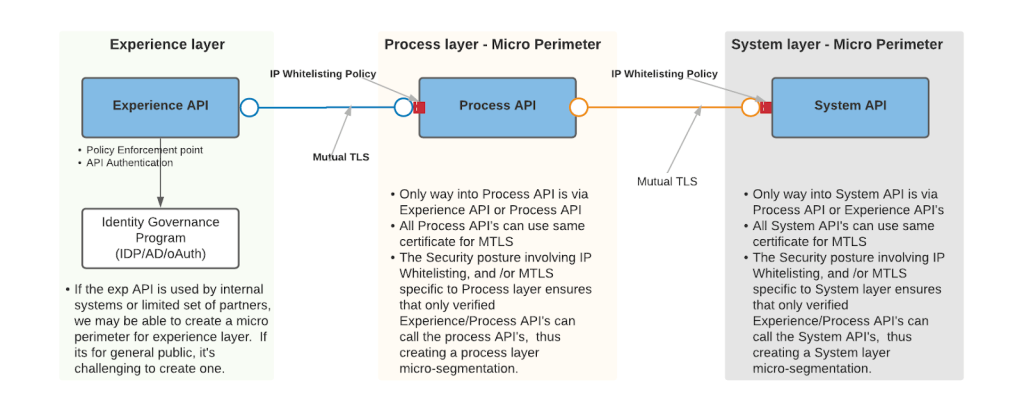
MuleSoft’s API-led connectivity enables micro-segmentation. Having a separate API layer for System, Process, and Experience APIs along with IP-allowlisting and MTLS between APIs creates a micro-perimeter at each layer as they restrict the access to API only via approved APIs, as shown in diagram below.
Using granular permissions
The granular permissions address restrict access to your API ecosystem. Depending on the sensitivity of the individual API, the following granularities could be enforced for a given request:
- Resource within an API
- Operation on the resource (GET, PUT, POST, DELETE)
- Location of the request
- Time of the day
- Day of the week/month/year
Most can be achieved by using appropriate out-of-the-box (OOTB) or custom policies in conjunction with a proper authorization server. Another important aspect to remember is to request access with the least privilege for a given operation, guaranteeing that even if a token is compromised, the impact is minimal.
Continuous diagnostics and mitigation
Security is never a “one and done”. As hackers continuously evolve their modus operandi to circumvent security measures, businesses must proactively monitor, diagnose, and mitigate security threats.
Some of the measures you can take in Mule are:
- Monitoring API policy violations to provide better insight into access attempts. This can be fed to SIEM systems to analyze the pattern to understand the intent.
- Codifying security, especially for granular permissions
- Performing regular penetration testing for all API endpoints
- Conducting regular code quality analyses to ensure code is not vulnerable to injection attacks
- Ensuring sensitive configuration data is properly encrypted.
Conclusion
APIs are critical entities in modern enterprises. MuleSoft plays a vital role in augmenting an agency’s zero trust security posture. Though there is no silver bullet to implementing zero trust architecture, following the aforementioned guidelines can help users easily implement ZTA for their Mule ecosystem.
As governments move closer to achieving a zero trust architecture strategy, the need for validated and secure data has never been more important.
Watch our webinar, How to advance your Zero Trust architecture strategy with secure APIs to learn from our panel of experts how government agencies are leveraging an API-led approach to achieve a zero trust architecture.
Catch it live or on demand:
- May 26, 2022 at 8am PT / 11am ET / 4pm BST
- May 27, 2022 at 11am SGT / 1pm AEST









