This blog aims at capturing different technologies and protocols in the IAM space and mapping them to Anypoint Platform.
Authentication, authorization, and access control are related concepts in Identity and Access Management (IAM). Authentication deals with understanding “Who are you?” whereas authorization is the means to figure out “What can you do?” Access control uses authentication and authorization mechanisms to enforce control based on actions and resources defined in a system.
Although basic principles could be easy to understand, often identity and access management are tricky. You’ve got a variety of use cases – everything from managing users across multiple SaaS platforms to managing access for API products and integrations. This blog aims at capturing different technologies and protocols in the IAM space and mapping them to Anypoint Platform.
Identity Management (AuthN)
With the digitalization of the modern world, more and more organizations are moving to the cloud, publishing APIs for external consumption, and adopting microservices architectures. An increasing number of target systems that include APIs and smart devices with or without human operators create new trends in identity space as well. Both user and machine identity play an important role.
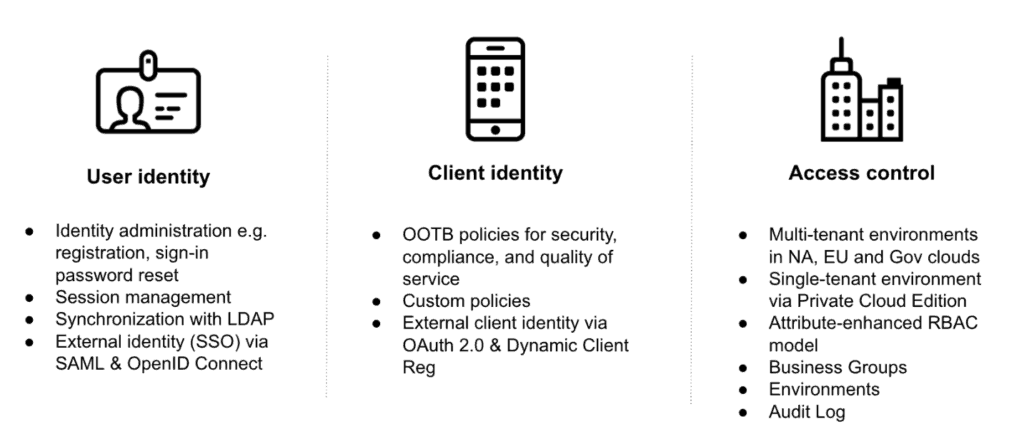
User identity
Security professionals understand that users want a simple, secure, and self-service experience when accessing their favorite services and APIs. By default, Anypoint Platform comes with its own identity provider (IdP). When users sign up with Anypoint Platform, they are creating an Anypoint identity, which allows them to access the platform, call APIs, and register client applications through an API portal.
To provide a seamless experience for both enterprise and community users, Anypoint Platform’s IdP supports the following features:
- Basic identity administration, such as self-service registration, user sign-in, and user profile updates.
- Session management, enabling termination of user sessions based on administrator configured settings.
- Password reset.
- Identity synchronization with LDAP (Private Cloud Edition customers only).
In addition to its own IdP, Anypoint Platform supports customers that are already using identity management systems such as Okta or Salesforce. In such cases, customers can either use an Anypoint identity or delegate the authentication to external identity providers to sign users into Anypoint Platform.

When it comes to external IdPs, MuleSoft’s methodology is to support the integration via standard protocols such as SAML, OpenID Connect, and OAuth 2.0. IdPs that support one of these protocols can be easily plugged into Anypoint Platform and used for user authentication. Today, Anypoint Platform IdP could be extended with one of the following identity providers:

Machine identity
As the number of API-enabled applications continues to grow, there is an increasing need for API protection and machine-to-machine authentication. Similar to authenticating users, machine identity is authentication on behalf of a piece of software, e.g., when one service invokes another service’s API.
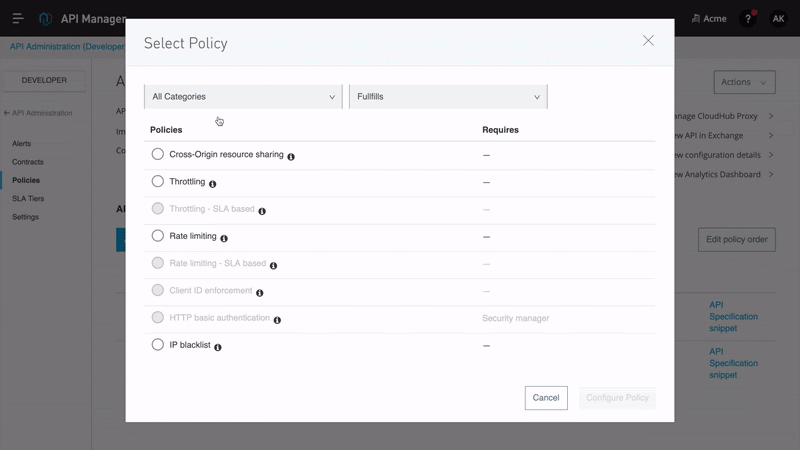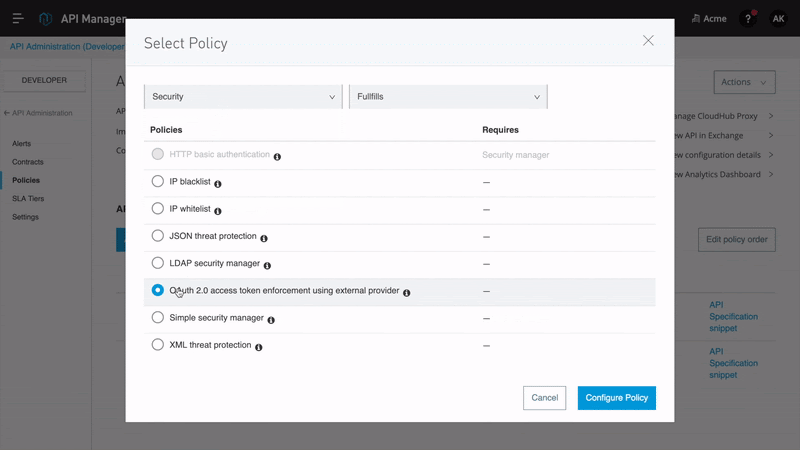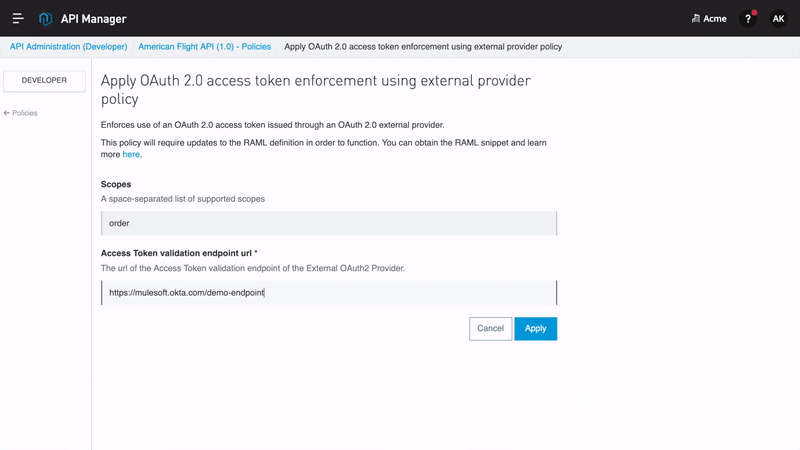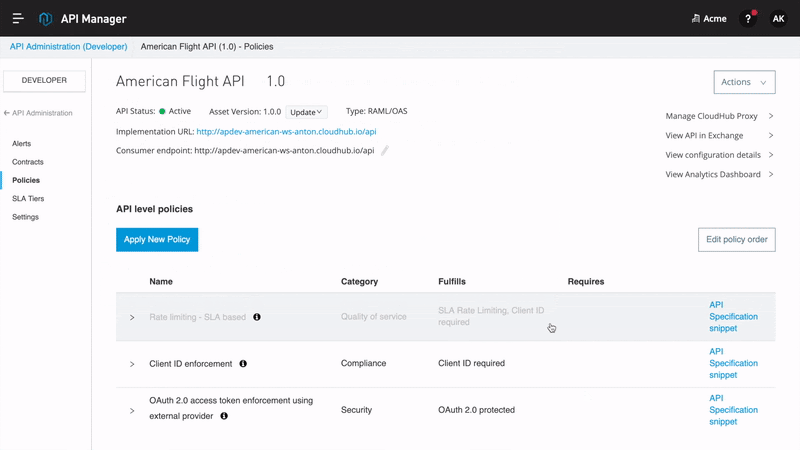
As organizations develop APIs for exchanging data with internal or external customers and partners, API providers have a variety of options with how to secure their API. To address these needs, Anypoint Platform includes Anypoint API Manager, which allows MuleSoft customers to easily design, secure, publish and manage their APIs. API Manager includes a library of pre-built policies that can be layered on top of an API implementation, enabling customers to tailor the levels of security, compliance support, and quality of service to their needs. Policies include OAuth 2.0, Client ID enforcement, rate limiting, and more. Additionally, API owners can design custom policies to meet their specific business needs.
Securing access via OAuth is a very common need among MuleSoft customers with API management needs. To address these needs, API product owners can use the OAuth 2.0 policy, which authenticates client applications and prevents unwanted users and machines from accessing data exposed by an API. In order to use an OAuth 2.0 policy, MuleSoft recommends using one of the OAuth providers listed in Tier 1 above. In such cases, API owners secure APIs with a policy using Anypoint Platform while delegating access management to an external IdP such as Okta or Salesforce. In addition to OAuth 2.0, a basic clientID enforcement policy could be used with or without an external identity provider.
Access Management (AuthZ)
Access management is a way of tracking, controlling, and managing users’ access to a particular system or application. To do this, authorization services use access control rules to decide whether access requested from particular authenticated users should be granted or rejected. Typically, an employee’s role in an organization determines the permissions that an individual is given within the system. This helps ensure that unauthorized employees can’t access sensitive information or perform high-level tasks such as altering production applications or APIs.
To address the above use cases, there are different models that realize access management such as Role-based Access Control (RBAC), Attribute-based Access Control (ABAC), as well as adaptive access frameworks that combine machine learning and advanced analytics. Let’s take a look at how these models are applicable to Anypoint Platform.
Anypoint Platform delivers access management functionality using a multi-tenant iPaaS environment, with an on-premises offering available via Private Cloud Edition (PCE). Multi-tenant environments are available in the US and EU regions.
To support a variety of customer needs, Anypoint Platform provides its own authorization service, which understands who the user is and what roles the user is entitled to. It employs an attribute-enhanced RBAC model where roles are created by grouping policies that dictate permissions. Organization administrators can create their own roles by changing attributes such as Environment, Business Groups, and versions of applications or APIs. These roles can then be assigned to users. In order to isolate assets, environments, and an ability to manage users and their roles through a user interface, Anypoint Platform provides Business Groups.
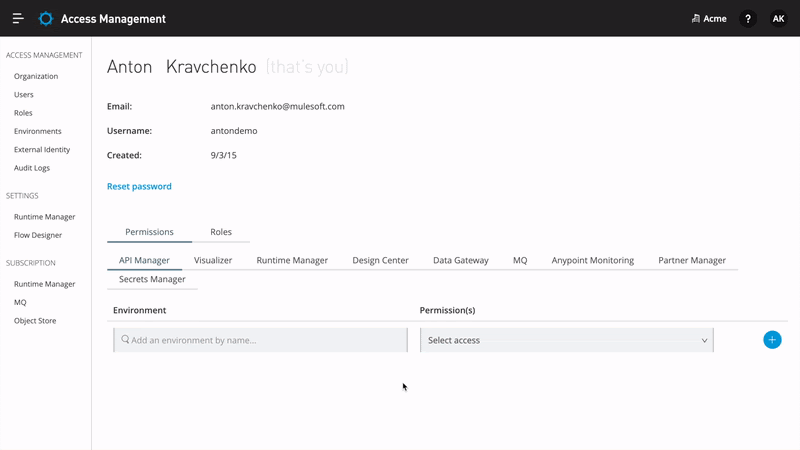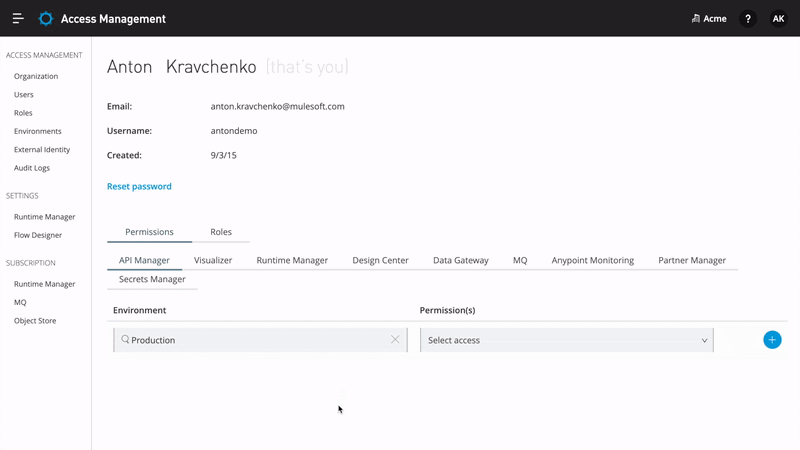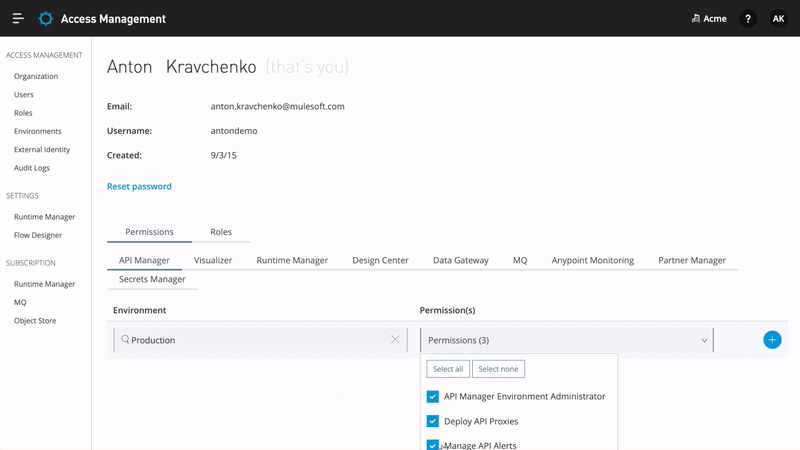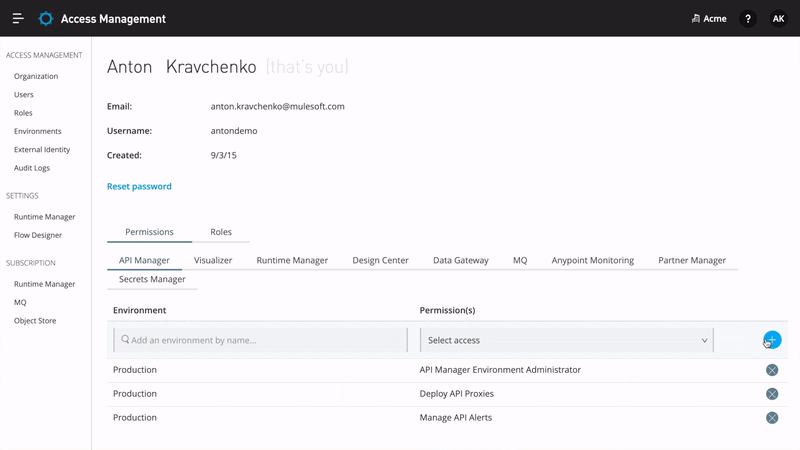
Anypoint Platform supports external or anonymous consumers that are not required to authenticate in order to interact with the Anypoint Platform. It enables users to expose external API portals for their organization, thus making their APIs visible to everybody on the web. Administrators can enforce further access, which will require external consumers to first provide identity before requesting access or calling an API.
Finally, administrators need to track all user actions within enterprise software applications in order to troubleshoot issues, understand user behavior, identify incorrect usage patterns, and detect security breaches or suspicious activity. Anypoint Platform captures key facts about what is happening via logs and provides users a log analysis inside Audit Log. Using a simple interface, administrators have a queryable history of all timestamped actions performed by users who have interacted with objects within their organization. Log data can be accessed through the Audit Logging Query API or through the Audit Logging UI.
Summary
In summary, to address an increasing number of use cases and needs around IAM, Anypoint Platform supports the following capabilities:
To learn more about API security best practices with Anypoint Platform, download our whitepaper, Protect your APIs.








