There are a variety of ways to establish connectivity between Anypoint CloudHub workers and systems deployed on backend customer-hosted or vendor-managed data-centers. One of the ways is through Anypoint VPN which provides a secure tunnel between cloudhub workers and a data-center. In order to setup the VPN tunnel or extend the CloudHub network with corporate network, we need to setup Anypoint VPC. Anypoint VPC provides an isolated network segment to host CloudHub workers.
Additional benefits of setting up a VPC includes:
- Control ingress access to the CloudHub workers via firewall rules.
- Provision a dedicated load balancer.
In this blog, I will demonstrate how to set up Anypoint VPC and VPN between CloudHub and Google Cloud platform and considerations to keep in mind while setting up Anypoint VPC.
Before getting started, you’ll need to be sure to have the following prerequisites:
- An Anypoint Account with access to provision a VPC.
- A Google Cloud platform account.
Setting up Anypoint VPC
Anypoint VPC setup is a self-service process and can be created either using the Runtime Manager or through CLI. For this exercise Runtime Manager is used.
- Login to Anypoint Platform and navigate to the organization’s/ business group’s Runtime Manager page.
- Select VPC from the left menu and click create VPC.

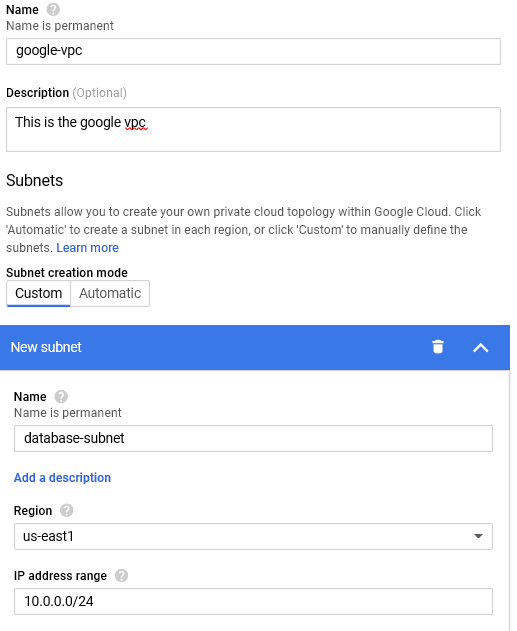
- In the following screen specify the VPC Name, Region, and the CIDR block. Refer recommendations below on setting up the CIDR block.
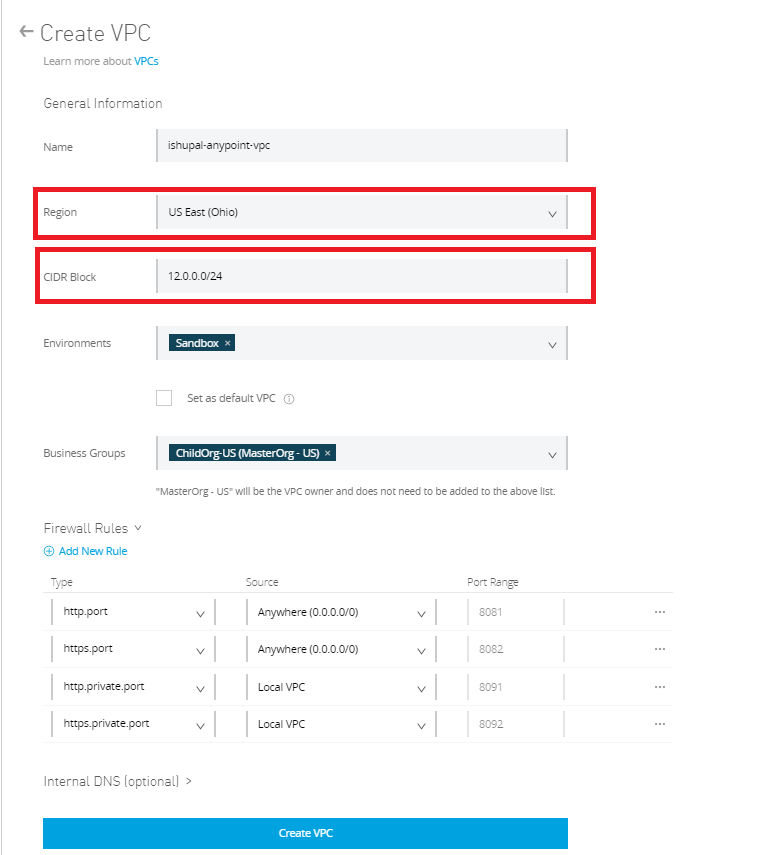
- Click finish and this will create the VPC. Any new apps deployed in the selected region will automatically become part of the VPC and get the Internal IP address from the CIDR segment.
- Define the firewall rules. For example:
- To completely restrict traffic from outside the VPN, remove the anywhere(0.0.0.0/0) and set it to local-vpc across all ports.
- To allow external traffic from a shared load-balancer, allow access to 8081/82.
- To allow access from DLB only, allow VPC access to 8091/92 only.
Recommendations:
- Select the VPC region which is geographically in the same (or near) the data-center or AWS region (for peering).
- Consider setting VPC at the organization level and sharing with other business groups. This is because VPCs can only be shared with child business groups.
- Separate the PROD VPC from the non-PROD VPC:
- Provides application/SDLC-level isolation and governance.
- Bandwidth dedicated to production and non-production instances.
- Cautiously size the CIDR range. Once the VPC is set up the CIDR cannot be changed. As a recommendation consider sizing based on the number of application instances (workers) per environment scoped for VPC.
As a good practice we recommend to keep current and future growth in mind and to size using the formula below for reference:
Maximum number of workers per app = W. We believe to set W=10
Number of apps = N
Number of environments in VPC the app will be deployed = M
Total number of IP addresses needed = 10 * N * M
Setting up Google VPN
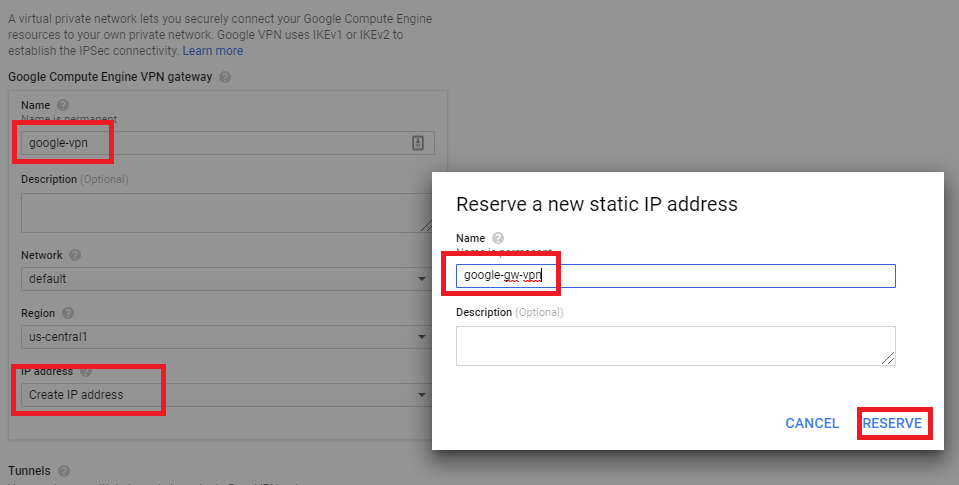
- Login to the Google Cloud platform and navigate to the VPN section.
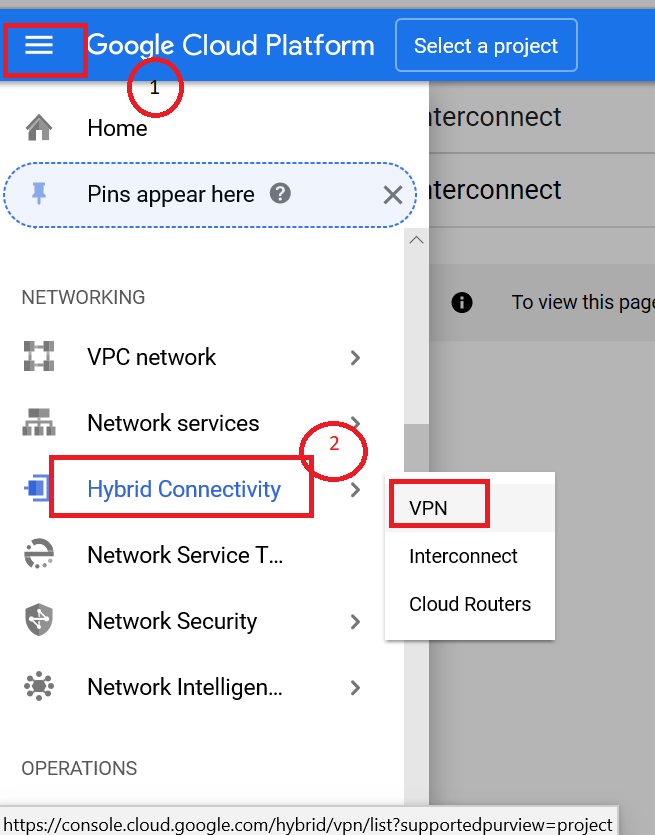
- Click create VPN connection.
- Select Classic VPN.
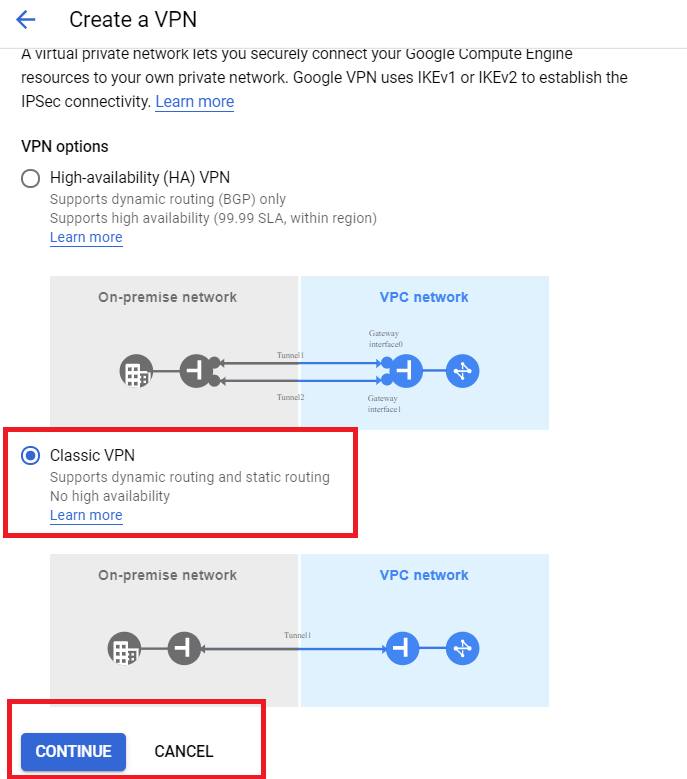
- Select the name and reserve the IP address. Note: The Anypoint VPC CIDR range should NOT overlap the GCP CIDR IP. range
Setting up Anypoint VPN
- Navigate to Runtime Manager and select VPN.

- Provide VPN name, select the VPC created in Step 1 and provide the Google Reserve IP address as the remote address. Provide the Remote and Local ASN number as per the screen-shot and select Routing also as BGP.
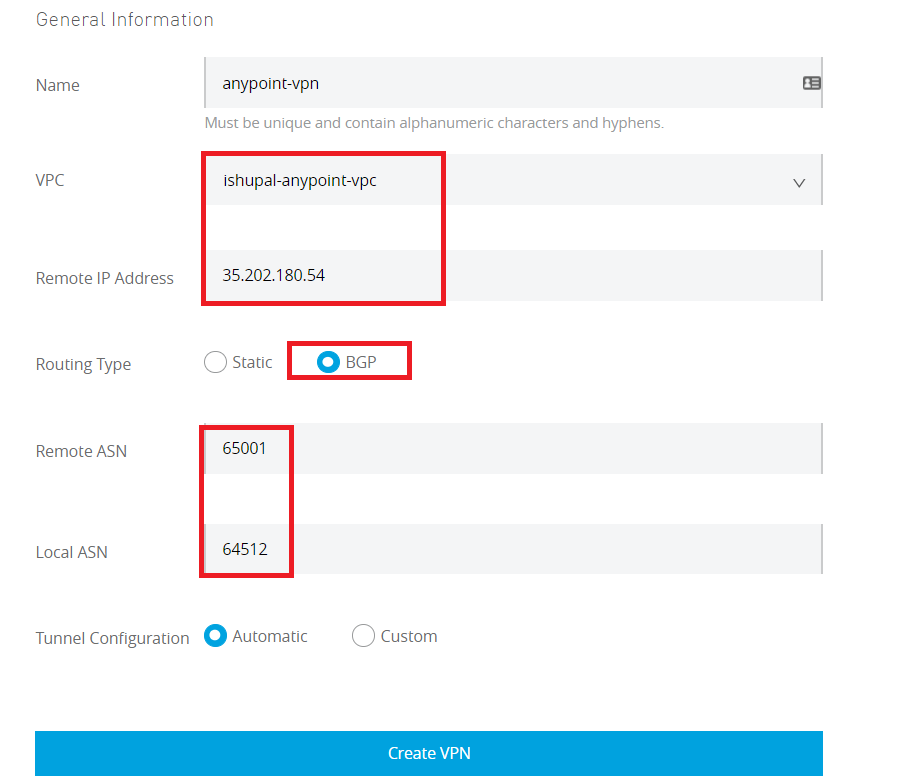
- Once the VPN is created, it will take a while to set up the tunnels. Once the tunnels are created, use the tunnel data to configure the tunnels on the Google side.
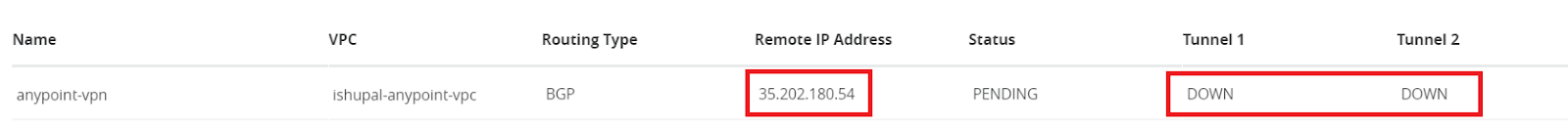
- Open the VPN configuration to retrieve the tunnel data. Google VPN tunnel setup requires the following from the Anypoint VPN setup.
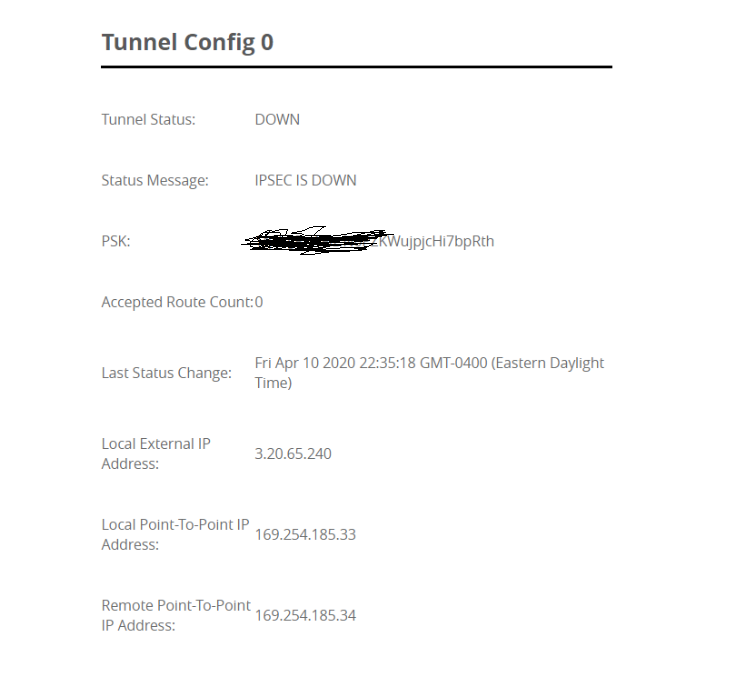
| Google VPN | Anypoint VPN |
| remote peer address | Tunnel Local External IP address |
| IKE pre-shared key | PSK |
Configure router and tunnel on Google
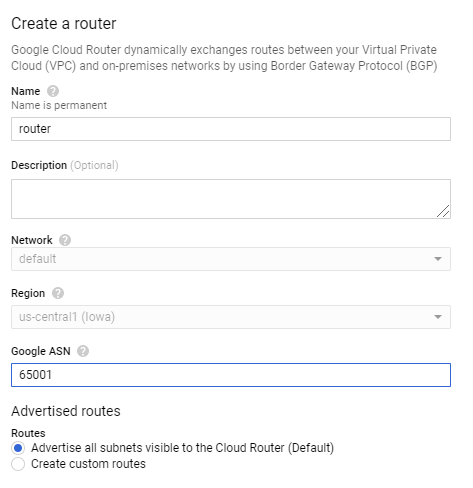
- Create the google router, provide the remote ASN from Anypoint VPN as the Google ASN.
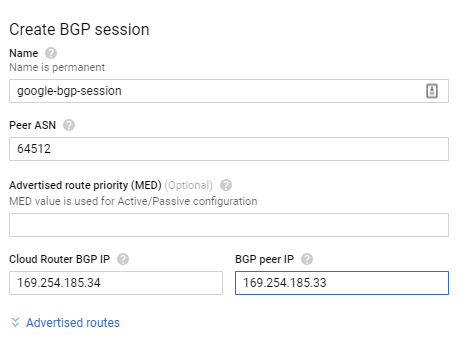
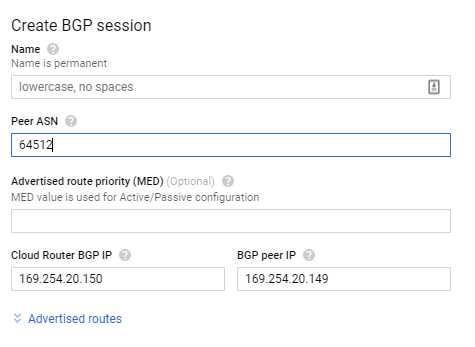
- Create the BGP session, use the Anypoint VPN ASN as the peer ASN session. And use the local and peer point-to-point address from Anypoint VPN to complete the BGP session configuration.
- Click create and the process will validate the BGP session. Once the validation is complete, the tunnel status should be established on both Anypoint and Google VPN side.
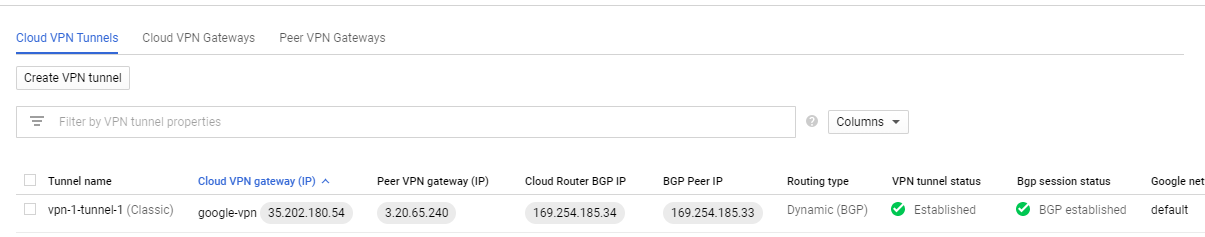
- Validate Anypoint VPN.
- Repeat the configuration for the second tunnel setup. Use the Anypoint Tunnel 2 configuration to set up the second tunnel on Google VPN.
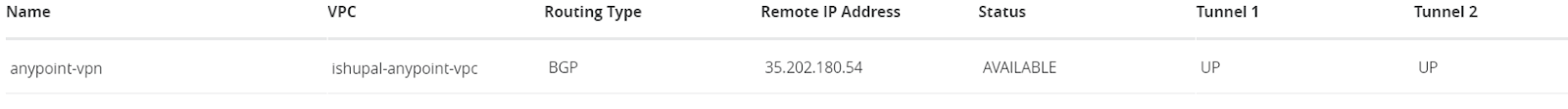
- Validate the tunnel status on Anypoint VPN.
- Validate the tunnel status on Google.
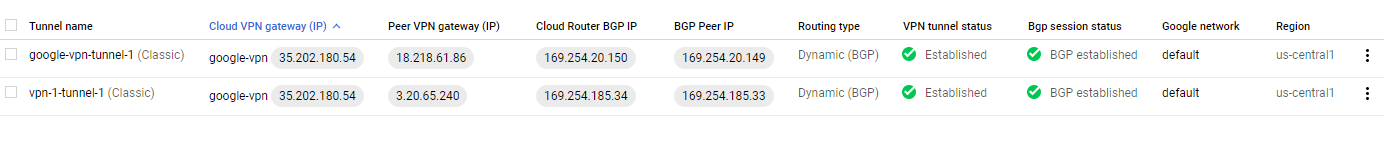
Note: In the above setup we used classic VPN on the Google side and the two tunnel setup provided the redundancy on the side of Anypoint Platform. However, if the topology requires setting up a high availability VPN on the Google side, we need to configure a separate Anypoint VPN. In that case, we will have four tunnels in all.
Now that we have the Anypoint VPC and VPN setup, any new application that we deploy (or restart) in a business group and environment associated with the VPC will get the IP address from the CIDR block. Once the apps are deployed in the VPC their accessibility can be controlled via the ingress firewall rules and we also get the ability to connect with backend systems deployed in Google Cloud (using VPN tunnel).
A few points to keep in mind are:
A few points to keep in mind are:
- Each Anypoint VPC is provisioned on one AWS region and exposes a VGW (Virtual Gateway) and can be attached to multiple business groups and environments.
- The MuleSoft VGW is associated with a single MuleSoft VPC but can support up to 10 VPN connections
- Once CIDR and region are associated they cannot be changed — any change will cause a downtime or manage complex routing mechanisms both at networking and application level (along with collaboration with networking team to reconfigure the connectivity with backend data centers, change in the DNS mapping for APIs routed through DLB).
- Each Anypoint VPN has one external address and is deployed on a specific region (example US-EAST, US-WEST) and provides two tunnels for HA.
- If the entire Anypoint (AWS) region or primary on-prem data-center goes down, applications running on the VPC will not work. Business continuity requires a comprehensive disaster recovery strategy — including VPC/VPN setup.
- Anypoint VPN supports both static- and BGP-routing for site-to-site internet protocol security (IPsec) connections.
- VPC peering and DX provide additional connectivity options with AWS.
If you still want to learn more about setting up VPC and VPN connectivity, please watch my Friends of Max video below.

This article provides the configuration steps for Anypoint VPN with Google Cloud HA VPN on Google Cloud Platform (GCP), using IKEv1.
The firewall settings on GCP must be configured to allow traffic from Anypoint VPNNote: The GCP documentation highlights this known issue when using IKEv2 – the larger SA payloads can result in IP fragmentation of the IKE packets, which is not supported by Cloud VPN. This can result in tunnel instability.
At the time of writing, there are no options to modify the Anypoint VPN tunnel options (to limit the ciphers sent in the proposals), and mitigate the issue.
While IKEv2 is supported, it is not recommended in this scenario.