DataWeave is a powerful language, and the possibilities of what you can do with it are infinite.
In this blog post, I am going to show you how to select specific data inside a series of specified XML tags.
For example, in this case we want to encrypt data inside sensitive XML tags such as an SSN, a credit card number, etc.
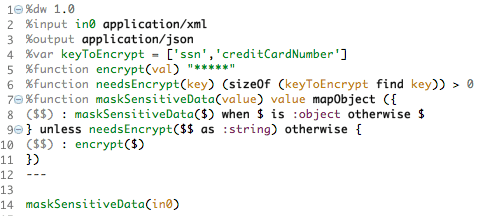
We define an array with the XML tags to be encrypted named keyToEncrypt (we are encrypting just the contents, not the whole line including the tag)
Then we define a function, to send the matching contents to a separate flow where the encryption actually happens.
After that, we define another function to determine if the tag we read is part of our keyToEncrypt array, if so, the sizeOf method will return a result greater than 0 (this ignores schemas such as <web:superTag>, the function will match anyway even if we just search for “superTag” alone)
Here comes the star of the show: the function maskSensitiveData will go through the tags and levels trying to match the element of our array, and when it matches one, it will send it to the function encrypt and re-assemble the XML tag content passed, replacing that data with “*****”, as we specified.
Here, instead of returning asterisks, you can easily call a (private) Flow that encrypts that data passed with your desired encryption method, using the lookup method.
It would look something like this:
%function encrypt(val) lookup(“encryptFlow“,val)
We create the encrypt function, which gives the passed val value, to the encryptFlow flow.
Here’s a link that helps you create an encryption flow using PGP: PGP Encryption Using Anypoint Studio
The full DataWeave code will look something like this:
For the ones interested in calling the encrypting flow with DataWeave, here is the DataWeave code with the call:
This way, we re-assemble the XML, but replaced the contents of the tags specified with encrypted/masked strings.
IMPORTANT NOTE: Always make sure that the mime-type that the transform-message component is receiving, it set correctly, in this case application/xml
To do this you can simply set it previously when you create the message that is going to be the input of that transform-message component.
Or you can force it in the configuration XML of the DataWeave input-payload:
Let me show you an example.
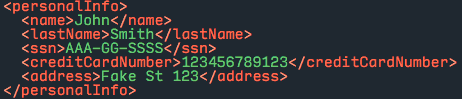
Let’s take this XML formatted personal information example we might want to protect, and run it through our DataWeave code:
The DataWeave code as seen on Anypoint Studio:
The data output as a JSON Array, as we specified previously in our output variable in the DataWeave code:
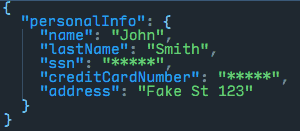
As you can see, the fields ssn and creditCardNumber, which were members of our keyToEncrypt array, are now masked with the specified “*****” mask.
This has been fully tested with:
- Mule ESB 3.7.3
- Anypoint Studio 5.4.2
Download the Full Working Example
Link to Download the Full Working Example: Download Now!