Reading Time: 2 minutes With the release of Mule ESB 2.2.7 (and the upcoming 3.1.0 ), you will see a reloaded version of the PGP module. The previous version was using the Cryptix library which currently RIP and doesn’t handle large files.
The new version uses the bouncy castle library which allows handling encryption and decryption using streams. We have added some integration tests that were necessary to update the library and the code safely. Also we have some time to do some memory profiling analysis.
To validate that the current implementation handles really complex and big cases we created a small example with 2 services:
An encryption service that reads files from one directory and outputs the encrypted file to a different directory. A decryption service that reads files from the encrypted directory and outputs the decrypted version to a different directory. The Mule config is the following:
<?xml version="1.0" encoding="UTF-8"?>
<mule xmlns="http://www.mulesource.org/schema/mule/core/2.2"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:file="http://www.mulesource.org/schema/mule/file/2.2"
xmlns:pgp="http://www.mulesource.org/schema/mule/pgp/2.2"
xmlns:vm="http://www.mulesource.org/schema/mule/vm/2.2"
xmlns:spring="http://www.springframework.org/schema/beans"
xsi:schemaLocation="
http://www.springframework.org/schema/beans
http://www.springframework.org/schema/beans/spring-beans-2.0.xsd
http://www.mulesource.org/schema/mule/core/2.2
http://www.mulesource.org/schema/mule/core/2.2/mule.xsd
http://www.mulesource.org/schema/mule/file/2.2
http://www.mulesource.org/schema/mule/file/2.2/mule-file.xsd
http://www.mulesource.org/schema/mule/pgp/2.2
http://www.mulesource.org/schema/mule/pgp/2.2/mule-pgp.xsd
http://www.mulesource.org/schema/mule/vm/2.2
http://www.mulesource.org/schema/mule/vm/2.2/mule-vm.xsd
http://www.mulesource.org/schema/mule/ee/core/2.2
http://www.mulesource.org/schema/mule/ee/core/2.2/mule-ee.xsd">
<spring:bean id="pgpKeyManager" class="org.mule.module.pgp.PGPKeyRingImpl"
init-method="initialise">
<spring:property name="publicKeyRingFileName"
value="./serverPublic.gpg" />
<spring:property name="secretKeyRingFileName"
value="./serverPrivate.gpg" />
<spring:property name="secretAliasId" value="6247672658342245276" />
<spring:property name="secretPassphrase" value="TestingPassphrase" />
</spring:bean>
<spring:bean id="fakeCredentialAccessor"
class="org.mule.security.MuleHeaderCredentialsAccessor" />
<pgp:security-manager>
<pgp:security-provider name="pgpSecurityProvider"
keyManager-ref="pgpKeyManager" />
<pgp:keybased-encryption-strategy
name="keyBasedEncryptionStrategy" keyManager-ref="pgpKeyManager"
credentialsAccessor-ref="fakeCredentialAccessor" />
</pgp:security-manager>
<file:connector name="fileConnector"
pollingFrequency="100000" streaming="true" autoDelete="true"
workDirectory="./tmp" />
<message-properties-transformer name="addPropertyS">
<add-message-property key="MULE_USER"
value="Mule server <mule_server@mule.com>" />
</message-properties-transformer>
<model name="pgpPerformance">
<service name="pgpEncryptFileProcessor">
<inbound>
<file:inbound-endpoint
connector-ref="fileConnector" path="./unencrypted" />
</inbound>
<outbound>
<pass-through-router>
<file:outbound-endpoint
connector-ref="fileConnector" path="./encrypted">
<transformer ref="addPropertyS" />
<encrypt-transformer name="pgpEncrypt"
strategy-ref="keyBasedEncryptionStrategy" />
</file:outbound-endpoint>
</pass-through-router>
</outbound>
</service>
<service name="pgpDecryptFileProcessor">
<inbound>
<file:inbound-endpoint
connector-ref="fileConnector" path="./encrypted"
fileAge="20000" />
</inbound>
<outbound>
<pass-through-router>
<file:outbound-endpoint
connector-ref="fileConnector" path="./decrypted">
<transformer ref="addPropertyS" />
<decrypt-transformer name="pgpDecrypt"
strategy-ref="keyBasedEncryptionStrategy" />
</file:outbound-endpoint>
</pass-through-router>
</outbound>
</service>
</model>
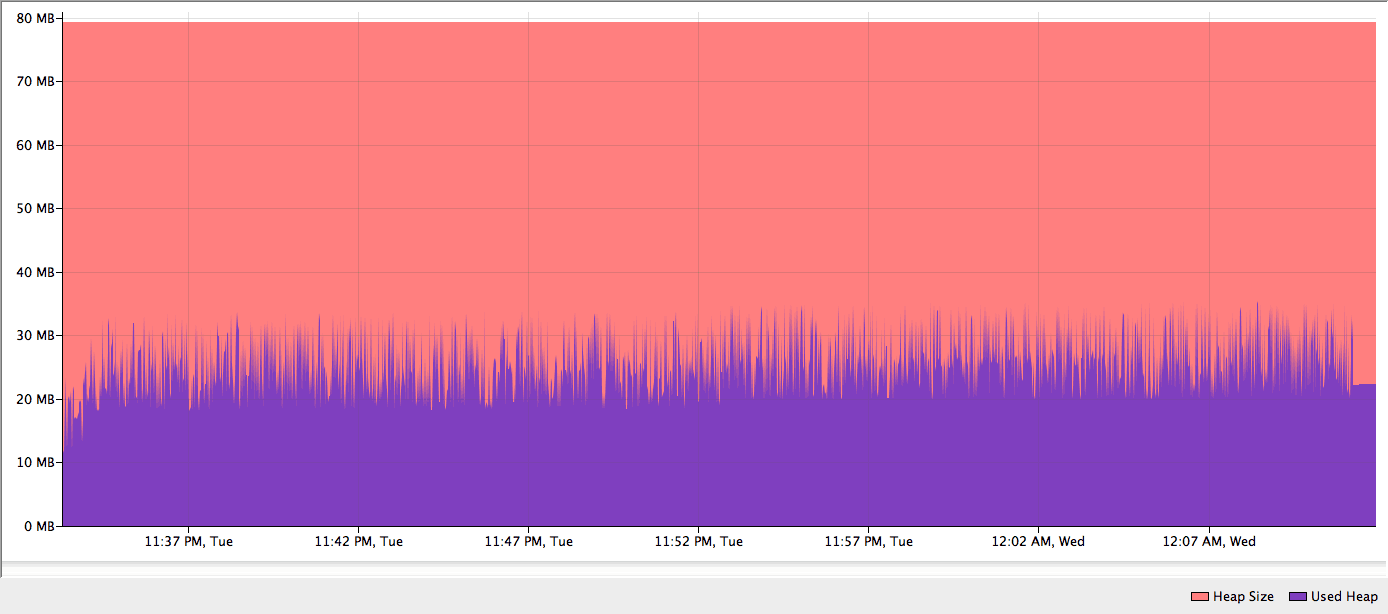
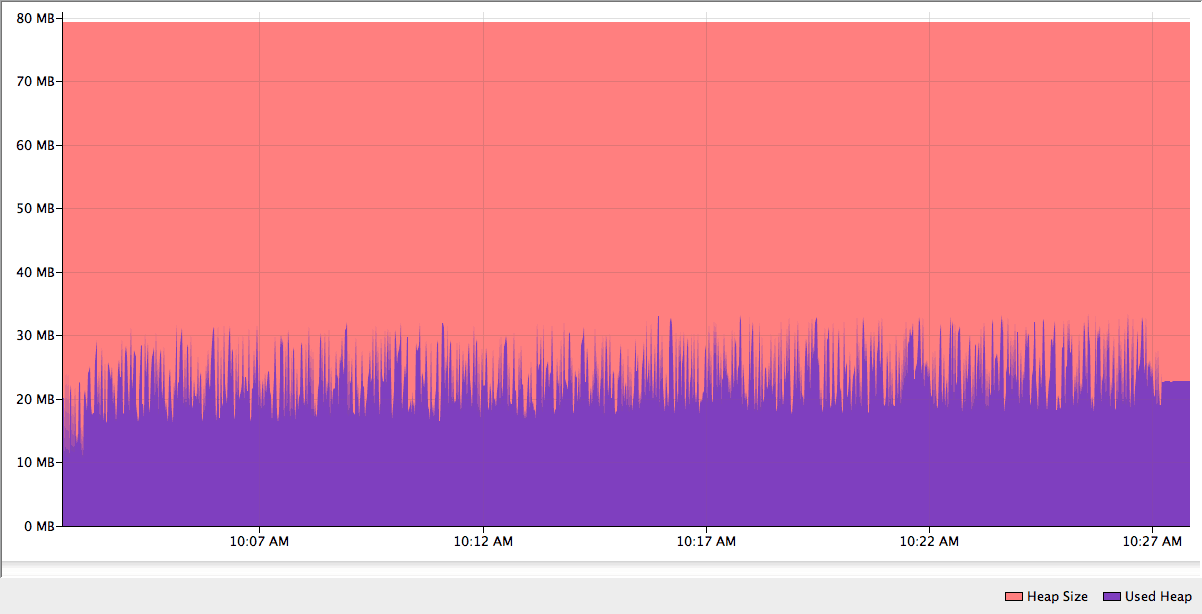
</mule>The memory profiling was done using a set of 23 files (12GB total):
12 of them are of 366MB. 11 of them are of 732MB. The following figures show that the new PGP module uses only 40MB for encryption and decryption:
Encryption :
Decryption:
Looking forward to hearing your comments!