You want to get more done in 2013 so you’re going to need to switch from synchronous to asynchronous processing to do more with the same resources. Mule started life as an asynchronous message engine and has a lot of capabilities and optimisations built in for processing data concurrently. To help you understand asynchronous processing in Mule we have created this cheat sheet that will help you understand the basics. Feel free to ask questions on this blog or on the forums. Enjoy.
Month: January 2013
Cheat Sheet: Asynchronous Message Processing
Handling File Attachments: handling multipart requests in Mule
Recently, I came across the following situation while working with Mule: I needed to handle an http post that would carry not one but N > 1 uploaded files.
If I were to do this back in the days where I didn’t know about such a thing called “Mule”, I would have needed to:
- Handle a http multipart stream
- Identify all the parts in the message
- Read each file
- Clean up
Of course there’re libraries and frameworks that can help you with this, but all of them still require some level of understanding of the multipart request beneath.
And then came Mule into my life, and this task became as simple as navigating the properties of a MuleMessage interface. Let’s explain a little bit….
As you probably know, what the MuleESB does is to carry packages of information (messages) from one system to another, allowing for software integration without the need of the involved systems to know about each other, their transport, protocols or any API changes. Each of those packages of information are represented by a MuleMessage. This object acts as a facade to access of a great deal of information about the message including, headers, payload and attachments, but today I want to focus on a property called inbound attachments.
When the message is coming through an http post that sends N >= 1 files through a Multipart Request, each of those files will be automatically read by Mule and stored in the message under the inboundAttachments property.
Pretty cool uh? No more worrying about Multipart, streams or anything like it, you just need to access this property as a Key-Value pair where the key is the filename and the value is the content itself. MuleMessage also provides a getInboundAttachmentNames() that returns all the keys.
So, let’s see a couple of examples. Suppose you want to retrieve the content of an expected file named foo.txt:
Now, let’s suppose that you want a flow that receives N >= 1 amount of attachments and logs all of them:
That was easy wasn’t it? If you’re thinking that this is pretty simple stuff compared to the average post in this blog, then mission accomplished! We have succeeded in demonstrate how easy it is to do every day chores using Mule. Please let us know if this post makes your life easier, that would really make us happy.
Get Loaded! With the new Dataloader.io
Reading Time: 4 minutes![]() We’ve just started 2013 and we already have something to celebrate! Dataloader.io January release is out with many improvements that will make your data loading life even easier than before, including:
We’ve just started 2013 and we already have something to celebrate! Dataloader.io January release is out with many improvements that will make your data loading life even easier than before, including:
> Related object exports – e.g. export contacts and their related accounts in a single operation.
> Filter exports by related objects – e.g. export accounts for a certain user.
> Create custom SOQL queries for advanced reporting.
> Friendlier error messages for data problems.
A New Year a New Mule
If you have queued up for more than twelve hours to see an opening-night showing of a Lucas- or Jackson-produced film, or slept outside to be the first to obtain a Jobs-ian product, or requested an invitation to pre-pre-order anything produced by Activision or EA, then you might be someone we’re looking for.
We want early adopters. We have a new, pre-beta version of Mule ESB, and we want to know what you think. Are we on the right track with our incarnation of a visual flow debugger? Will our DataMapper enhancements be welcome improvements? Was it a good idea to include an animated paper clip to offer assistance when building a flow? (Just kidding.)
Download Mule and give us your feedback. While not production ready, this version is something in which to discover, to explore, and to constructively criticize. Get your hands dirty. Try it on for size. Give us the feedback through the forums or commenting on this post.
Want to see the movie trailers?
Visual Flow Debugger
DataMapper Enhancements
We’ve also added a few features like connection management, documentation generation, and transaction demarcation to improve the lives of integraters everywhere. Read the blog post that accompanied the initial December 2012 launch of Mule ESB 3.4 early preview to get a full account of all the juicy details.
Think you know Mule? Think again. 2013 is going to be interesting.
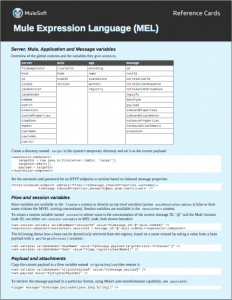
Cheat Sheet: Mule Expression Language
Since Mule 3.3 the Mule Expression Language (MEL) has been the default scripting language for expressions in Mule. It is very powerful and based on the MVEL language (note you can also use JavaScript, Groovy, Python and Ruby). MEL provides a very easy way to access the current message in a flow, write conditional filters and perform content based routing. The MEL Cheat Sheet, gives you an overview of the commands you can use.
Other Resources
- Mule Expression Langauge Reference Guide
- Using Mule Expressions
How to Protect Your APIs with OAuth
On this 10th ‘Day of Christmas’ Mule blog post, we tackle an increasingly important question in the world of APIs: Presume that you would like to create a remote API (which perhaps exposes some legacy business logic) for access by internal and/or external clients. How can you make sure that access to your API is protected in such a way that:
A) Only clients that you trust can access them;
B) Those clients can access your API through the explicit authorization of their end-users; and
C) The end-users can be authenticated with a central entity, *withouth* having to share their credentials with your API’s clients.
It turns out that over the last couple of years, as the prominence of remote APIs, specially REST based ones, has increased, the need for a good answer to this question has become critical. At the onset, to address the question, many proprietary web authentication protocols were created (AuthSub, AOL’s OpenAuth, Yahoo’s BBAuth, and others…). OAuth is a security model which brings together the results of such existing bodies of work to address this question in a common manner.
One of the most impressive elements of the Mule Enterprise Security (MES) features that we introduced at the beginning of December is the support for OAuth. Specifically, with MES, you can make Mule act as a full-fledged OAuth 2.0 provider (the latest version of the spec which has recently officially become a standard!) and use it to protect your backend APIs.
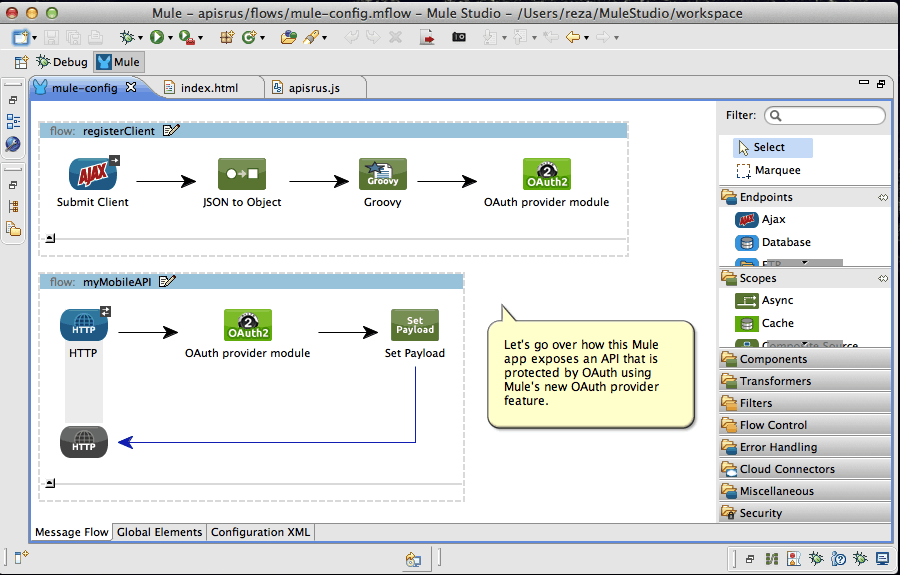
To show how easily this can be done, we have put together a sample Mule app that shows how, with only a couple of lines of XML, an HTTP API exposed by a Mule flow, can be protected with Mule’s OAuth 2.0 provider. The example also contains a simple JavaScript based Web client that walks through the OAuth dance and shows how clients (say a Mobile app) can interact with the OAuth provider in order to obtain a secure token and access the API. The following diagram illustrates the different elements of the example:
To better understand how the pieces come together, have a look at the following short viewlet which goes over the example and demonstrates its use.
This example is only the tip of the iceberg as far as the capabilities of the Mule Enterprise Security OAuth 2.0 provider are concerned. There is much more, including support for Role Based Access Control (RBAC), scopes, other OAuth 2.0 grant types, as well as the ability to protect APIs that are not necessarily exposed by Mule flows. I am planning to go over these other capabilities in upcoming Mule blogs – stay tuned! – but for now, hope you enjoy this simple example illustrating a very powerful capability recently introduced in Mule.
Note: To try out the example described in this blog , you need to install Mule Enterprise Security first. Only then you can import the example into Mule Studio (versions 3.3.1, 3.3.2, and 3.4 M2 are supported).
Introducing MuleSoft Blueprints: Scalability and Availability
One of our New Year resolutions is to create more content around specific subject areas. The aim of MuleSoft Blueprints is to provide a complete guide on a specific topic in a way that can be easily read and kept for reference.
To get you started we have a preview of the Load Balancing Mule for Availability and Scalability. This blueprint will introduce the necessary concepts and show how to achieve availability and scale with JMS, Mule HA, VM queues and more. This is a preview, we’d love to get your feedback on format, content and topics, you can reach us in the forums or just comment on this post.