Judgment day for API attacks: Spotting the friendly robots amidst the foes
In part one of this blog series, we covered the robots driven to disrupt your business and online operations (DoS and DDoS attackers). In
Terminating API attackers so they won’t be back
Wow. My head is spinning. Every week there’s a new breach. This week, Peloton got caught asleep at the wheel and had to bow
How and when to implement dedicated load balancers
This blog will cover the architecture of the dedicated load balancer and the importance of the mapping rules in the dedicated load balancer with
Securing the public APIs you didn’t know you had
With the accelerated pace of digital transformation following the dawn of the COVID-19 pandemic, many organizations and leadership teams are asking themselves this question:
How to choose the CIDR block for your VPC
In one of my previous blog post, we saw that creating a VPC is quite simple. We just need to provide values to four
How to use a VPC to isolate your worker instances
CloudHub is the cloud-based iPaaS component of Anypoint Platform. Applications on MuleSoft Cloudhub are run by one or more instances of Mule, called workers.
How many VPCs do I need?
In my previous blog post, we explained the different scenarios required to get a VPC in place. But there’s yet another question we need
Do I need a VPC for my Mule apps?
One of the first tasks to set up your Anypoint Platform is the definition of your network architecture and in particular your virtual private
Privacy data management is the Achilles’ heel of every IT organization
Privacy data definitions are expanding, regulations are proliferating, and customer expectations regarding the use and protection of their data are rising as well. CIOs
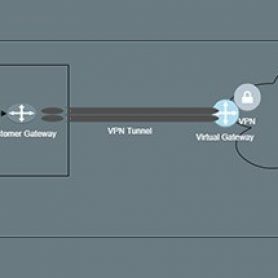
Setting up Anypoint VPN with Google Cloud Platform
There are a variety of ways to establish connectivity between Anypoint CloudHub workers and systems deployed on backend customer-hosted or vendor-managed data-centers. One of